
Network Management Guide
In this network management guide I try to talk about the basics of everything that goes into managing and monitoring a network. I will talk about monitoring most aspects of you network along with things to do to help it.
Network Management
In network management there are many details to keep track of. Monitoring is a huge task but it is one that needs to be done thoroughly. There are many ways to do it and tools to use. This guide talks about many of the requirements that you will need to monitor.
Network Monitoring Tools
A packet or protocol analyzer is one of the first tools that we can use to examine a network. They can display, capture, and save packets. This software can read packets intended for other devices. If it is used in promiscuous mode then the packet sniffer is seeing the information pass across a network.
One of the most popular example of protocol analyzers is called Wireshark. It is very popular because it is free and works quite well. It can specify which network interface is to capture packets. You can operate it in promiscuous mode to see all traffic. The software can define what types of packets are to be captured. Finally, you can tell Wireshark how long a packet capture should run before it terminates the connection.
Scanning Tools
A port scanner is another type of tool to look at a network. They can examine specific machines to check for open ports. If you see a port scan hitting your server then it often means that someone will try to attack your network. The person that is doing that is trying to find open ports on your machine. If he can do that then he will then see if you have anything vulnerable.
When analyzing your own network you need to see what machines are generating the most traffic. This will often be a clue as to what machines are compromised if the traffic is a lot more than usual. However, you will have to do this over a period of time to establish a baseline for traffic so that you know what is out of the ordinary.
Packet flow monitoring gives an overview of the traffic. A flow is the network traffic between two different machines. We want to use this monitoring because it gives us a good idea of the usage on parts of out network.
SNMP Network Management
This is simple network management protocol. It is used for network management and it is very useful. It is the standard for management and it is very popular. SNMP agents are put on all your machines you want to monitor. This application tool will then occasionally ask the agents on those machines whether everything is working as intended or not. You can configure your application to ask once a minute or once every hour. It will be up to you to decide what is best for your environment.
Common devices that need monitoring are routers, switches, and servers. Keep in mind that you need actual enterprise network gear to has these capabilities. You can not go to your local office store and get a router there that will be able to do this.
Since we know that the management software can ask the agents for information we will need to display that information in a nice way. Messaging can be configured to give us the information that we need.
There are a few different versions of SNMP so use the most current if possible for security purposes.
System Logging
All modern operating systems have system logging included. We need this on our servers so that we can go back and look at these logs to see what is happening. These can be generic operating system logs, database logs, or various application logs. It is important to look at them occasionally to make sure nothing is different or weird in your systems. However, they are a great place to start when diagnosing problems.
They can be very resource intensive so monitor that when you can. We use these to see what is happening on any given day or minute of a day.
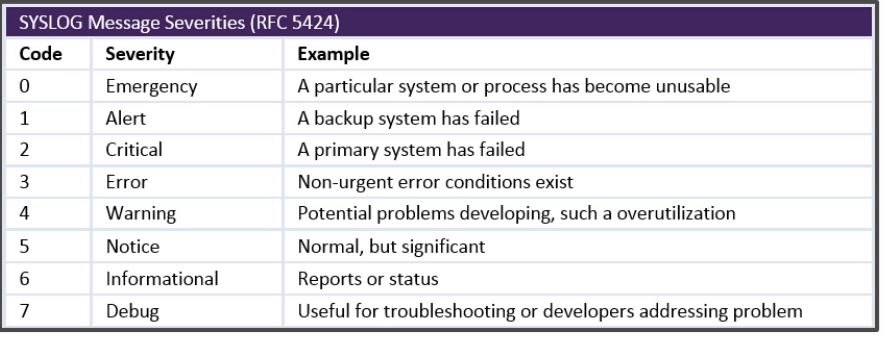
SYSLOG is important to know about. It is a standard for logging and reporting. It has error codes from 0-7 with 0 being the worst and classified as an emergency. The SYSLOG software functions as a server. This is nice because applications can send their local logs to this remote server. It will collect and make things easy to analyze.
Monitoring alerts can be sent to anyone that requires it. SMS messaging is often chosen and convenient. This allows administrators to be on call and responsible for their systems.
Environment Monitoring
Conditions need to be monitored in your network closets and server rooms. The rooms do not need to be too hot, cold, or humid. So we need to keep them within a safe operating range. These locations should be monitored for temperature and humidity. The solution tot his is to add sensors that connect to our network. These sensors should have SNMP and alerts so they can tell the administrator when something is wrong.
Power is another thing that should be monitored. The UPS's should have SNMP as well ti send out alerts if power is failing or conditions that are bad. UPS's can also provide limited power for servers so they can be shut down normally. However, this only works if we know that power conditions are bad so getting that first alert nice and quick is what matters here.
Wireless Surveying Tools
Another topic that is important these days is WiFi interference. We all have several devices that operate with WiFi that we need to know how to help our signal and make sure that our equipment is operating correctly.
Your work space should be monitored to make sure your wireless signals are getting to all the places they need to. The signals should be strong so users can do what they need to do. It is helpful to make a map for reference using an online drawing tool. Label where the signal is good and also where it is bad. Elevators and other metal structures are always bad for wireless signals. They can not get through metal so people on the other side could have bad reception.
There are specialized tools that can help us take a site survey. These tools can be software or they can be hand held devices that many vendors make. These are called wireless analyzers. They are used for troubleshooting insecure networks, connectivity, and doing reports on a network.
Getting A Baseline For Network
When we are baselining a network that means we are getting its normal behavior. We want to see the usual traffic and issues on an average day. That way we know when something is out of the ordinary. This should include knowing our hardware resource utilization of devices like our workstations and laptops. Knowing the bandwidth that our devices use is also very important.
When taking a baseline you should do them at different times of the day. This means that you should measure activity on when the network is slow and also when it should be busy.
Network Telemetry Logging
Every operating system has different telemetry tools available. It is important to use these often know what is happening on key machines. You can analyze traffic going in and out. Seeing what spikes your network traffic is also important.
Analyzing Network Utilization
While we always hope our traffic is moving quickly we sometimes get bottlenecks. It is a component with a lower capacity than the rest of the system. It is what is holding the rest of the system from going faster. In a machine it is often the hard drive that is the slowest part of the system for example. That is a bottleneck.
Bandwidth usage is important for our WAN connections. WAN is of course our wide area network. When WAN traffic is unusually slow we may have configurations issues at our router or gateway.
We should also monitor our storage. SAN's are a popular type of storage for enterprises. A SAN is a storage area network. Tracking the usage of our storage is very important to ensure users have what they need.
CPU and memory usage are other attributes that should be monitored. If there are bottlenecks in any of these areas then we may need to upgrade certain devices or components.
As mentioned above, analyzing our wireless is also a good idea. Most traffic is on the 2.4 GHz section instead of the 5.0 GHz spectrum. There are many channels that can overlap and cause issues if they become too crowded.
Analyzing Network Interface Data
Monitoring interfaces for their link status is helpful. This is communicated back and forth to your software. You can also look at the devices to see the status. For example, printers and workstations have network cards in the back with lights on them to indicate status. This is helpful when troubleshooting issues. SNMP enabled devices will also report when a link is down.
Device and workstation interfaces can be monitored for more than its link status. Over time, errors and dropped packets can mean you have a more serious issue. High usage over time can mean you have driver or software issues.
The interface speed on a device must match the device it is connected to. However, most ethernet devices support a range of speeds and will go back to the speed where everything works.
Configuration Backups
As your network grows it is important to save the configuration of your devices. This is very helpful when moving them around or replacing them. Most devices can backup their configurations using TFTP or trivial file transfer protocol. After backing up all your data you need to protect those files. This is called data archiving. It is the storage of data securely off for long periods of time. This data archive should be at another location.
If a natural disaster happens like a tornado then network devices can be brought back to their original state.
Managing Configuration Baselines
Configuration baselines specify a functional state for a device. Baselines are useful in configuration management to establish a configuration state and define a change in configuration. Baselines can be used in auditing to confirm configuration status.
Server machines can be configured to automatically get updates to reach a baseline level. Data center management software can automatically take servers offline, fix any issues, and then bring them back online. If a device does not meet pre-defined standards then it must be brought to the level where it does. This process can be automate depending on the device and software.
Mobile Device Management
Smart phones and tablets are being used more and more in the workplace. You need a way to manage all these devices when they attach to your network. People are using these devices because they are easy to use and very portable. I use my smart phone for tracking work orders and many other things when I am not at my desk. They are very useful indeed.
Exchange server can be used to communicate with our phones to give us our corporate email and calendars. Our management software needs to be able to remote wipe devices that might be lost or stolen. This protects our network. Devices should also support encryption.
Mobile devices all need to connect wirelessly. That means our network needs to provide proper signal everywhere its expected. Businesses often incorporate a guest wireless network for this reason.
Network Access Control
A NAC is a network access control. It is a method of ensuring connecting devices meet our network policy. When machines or mobile devices connect to our network we can make sure that it meets certain standards.
A network access control will usually check for antivirus, operating system updates, and make sure the firewall is enabled. NAC's will quarantine systems if they do not meet certain standards.
Documenting Your Network
Documentation is always important. You should document everything you can. Network configuration is especially vital. Configurations of your firewalls and switches should always be done. You should document your server and cable closets. Labeling cables that go into switches is also very useful.
Documenting your IP's is something every network admin should do. This lets you now what is happening and lets you know how to access everything on your network.
Assets should be documented too. Every significant device needs to be on a list somewhere to keep track of what you have. This will let you see if everything has the same patches and operating system.
Asset management software should include ID's, locations, and software versions.
Industrial Networks
An ICS is an industrial control system. They control industrial systems that are in warehouses or plants. You also see them in energy, power, and water plants. They are often networked but do not provide access to the outside internet.
Private Networks
A common plan for security is to use private addresses on your lan. Everyone does this now and it is common practice. The reason why this helps is that these private addresses are not directly accessible from the internet.
Security for your network should have many layers. Firewalls should be there too obviously. They will filter traffic that comes in. Firewalls should be host based and at the endpoints to cover everything.
Reducing Network Congestion
One way to help with congested network traffic is to segment different parts of your network from the rest of it. For example, if a particular device or server uses a lot of bandwidth then it could be moved over to a separate network segment so that it does not interfere with the rest of the network traffic.
Load balancing can also help with network traffic. This is useful when you have tons of network traffic. I can be used to split loads between servers to help with congestion.
Conclusion
There are many things to consider for network management. You have monitoring of a lot of different aspects. There is security to consider. Making your users happy with the right level of performance is also a necessary consideration.