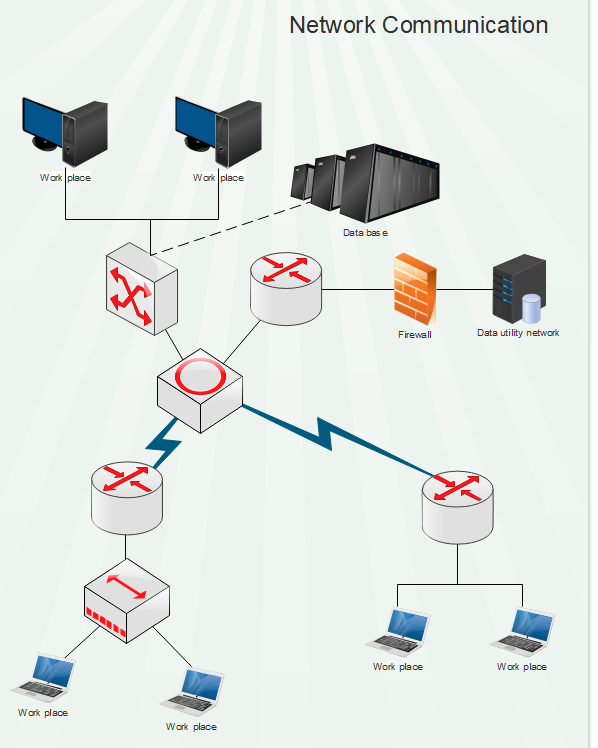
Guide To Network Communications
A computer network can handle a lot of different roles these days. Essentially it pushes data around to devices and controls what happens. Some of the more interesting uses for a network now is VOIP communications and video conferencing. In this guide to network communications I go over some of those details.
Guide To Network Communications
First of all, the network communications in a business or organization can take on many forms. A business or individual may use part or even all of these types of communications. In conclusion, they each have their use cases and advantages.
- Voice over IP.
- Video broadcasts.
- Surveillance.
- Collaboration software.
- Quality of Service.
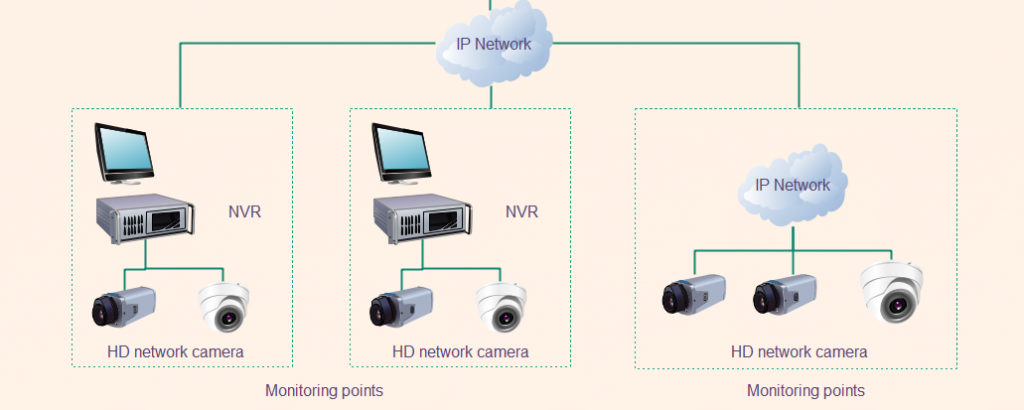
Voice over IP
Voice over IP is used in many if not most business environments today. You can get a lot of cool features with these types of phones and save a ton of money over traditional phone services. Another reason this has become so popular is because it uses the same Ethernet cabling as the rest of our network.
Video Broadcasts
Video of most varieties can also travel over the network, so others can see it. This can be a streaming event like a webinar or just something made locally by a department that needs to be seen by the entire organization.
Surveillance
Surveillance and security cameras are also part of this. They may not get sent out as videos very often but the footage sometimes needs to be seen. Among your typical network communications this is often the most important but also the least used.
Collaboration Software
Another nice advantage of network services is collaboration software. This can be something that helps with documents or even some sort of chat software like Cisco stuff or Slack.
Quality of Service
Quality of service is essentially several mechanisms working together to guarantee delivery of time sensitive packets. This is important because too much data loss with one of the previously mentioned services will cause it not to work. Furthermore, we need a quality of service that is at least to a certain point so we can do our work.
- Data can be classified by address or application type.
- Once it is classified it can be prioritized by the traffic type that works for your business.
- For example we can make voice traffic a higher priority than other types of traffic.
Network Virtualization
Virtualization allows you to connect virtual machines and devices to a network in the same way that you connect physical devices. You can connect these virtual machines without using a physical network adapter. Consequently, this is becoming one of the most important types of network communications as it is becoming central to all that we do.
- This makes it easy to build a complex network.
- No need to invest in a large amount of expensive physical hardware.
- This model supports a high number of virtual networks on just one physical network adapter.
- These networks and network devices will use our current DHCP server.
Virtual machines connect to a network through a computer with a network adapter. It can connect to all computers connected to that network adapter. Without using a network adapter it exists as part of an internal virtual machine network. This process does require virtual components to function which acts in a similar way to their physical counterparts in a physical network.
Network Virtualization Devices
A virtual switch allows you to connect virtual servers to separate lans. Since they behave the same as a physical switch a virtual switch allows you to separate traffic for security and quality of service reasons.
This virtual device will also allow you to route traffic between devices just as a real firewall would.
- Virtual firewall
These filter packets and monitor traffic.
Storage Area Network
This is any high performance network whose primary purpose is to enable storage devices to communicate with computer systems and with each other. This gives us fault tolerance and redundancy with our storage.
- Storage devices provide access to shared block level data storage.
- This is used to make storage devices accessible to servers so that the operating system sees them as locally attached devices.
- The server accesses the storage at the block level.
- The storage appears locally attached like an internal disk.
Fiber Channel
Fiber channel is often used as the network communications protocol in a storage area network. A storage area network is often made up of multiple fiber channel switches.
Network Attached Storage
This is a file level data storage device. It will not appear as a local storage device.
- It attaches directly to a network much like computers and servers.
- Provides data access and file storage to computer systems on the network.
- Effectively replaces one or more file servers by providing the central storage locations for users data.
- Accessing data storage from network attached storage is done over the IP network using file level protocols.
- The operating system level of the computers and servers do not appear to have the data storage available locally.
- Users have to access data as a file share over the network.
- Creating file shares on the network attached storage devices enables other computer systems to connect to the shares.
Cloud Computing
Cloud computing provides access to network communications resources such as services, applications, servers, network infrastructure, and storage on a distributed network. Therefore, this is all on the internet and is basically someone else's resources.
- Users access these resources by networking and various internet protocols.
- There are several service models we use in cloud computing and each has their advantages.
- Infrastructure as a Service (IaaS) is physical devices.
- Platform as a Service (PaaS).
- Software as a Service (SaaS) include any kind of application.
- the hosting provider owns all of this physical infrastructure and rents it to you.
Infrastructure as a Service
Infrastructure as a Service is talking about your physical devices. It is the lowest level of the network communications. This can be routers, switches, computers, printers, storage devices, power units, racks, locks on doors, and cooling. You can see there is a lot to it. All of this is essential though.
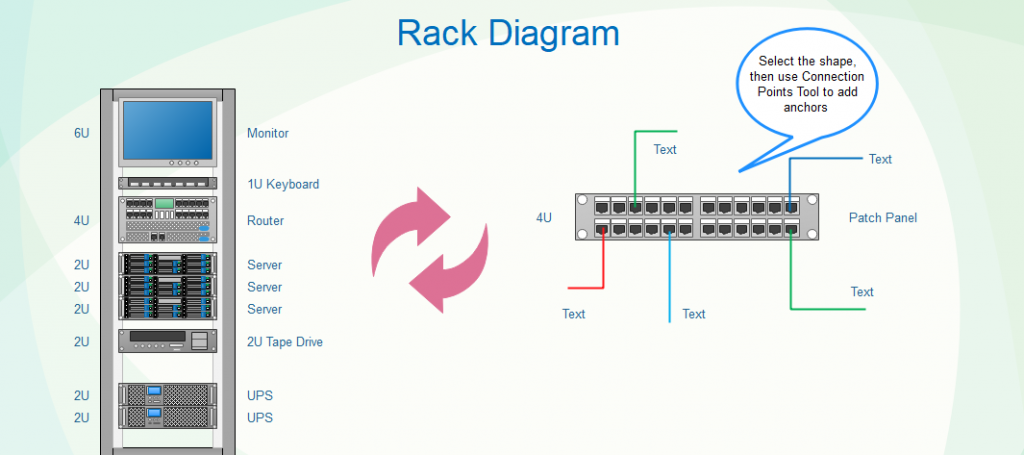
- This infrastructure can replace aging units in your office.
- You can have a separate site that is a backup in case your main office goes down.
- This can also fulfill a temporary need for resource expansion.
- It can help you spread out in other geographical areas.
- You can use infrastructure to help with increased loads to a server.
- If you have a short lived project you can rent infrastructure to help and give you more computing power.
Platform as a Service
Platform as a Service sits just on top of the infrastructure. This usually deals with virtualization and the operating system layer. A platform can be Windows, Linux or BSD. Virtualization refers to a type a hypervisor such as VMWare, Hyper-v, KVM, or Xen.
- The cloud provider is the owner of the platform and as a customer can make use of it.
- The cloud provider manages the installation of the operating system and the hypervisor.
- It can be used for temporary acces to the physical infrastructure and operating system.
- If you do not have the skills to use KVM for example you can let a provider manage this for you.
- You can also rent this if you have a general lack of maintenance skills.
- It can help with development and testing if you do not have the resources in house to do it.
- This gives you access to that infrastructure that runs it and also gives you a backup for your running applications.
Software as a Service
Software as a Service is the top layer of the overall cloud infrastructure. This functionality offers complete applications to the cloud user. A good example of this that most people use is hosted email.
- More examples include web applications, file sharing, business applications, and music services.
- The cloud provider proves access and maintenance to the application.
- We can use this when we want to avoid application and software maintenance tasks.
- Another time is when we have outdated software and not enough money to buy new licenses.
- We can use software as a service if we lack the skills to support the existing applications.
- It allows us to focus on the business side of things without hiring an IT department.
- Costs can be greatly reduced by using software as a service because we do not have to have all the infrastructure and people to run it.
- This is also useful to help with testing applications.
Cloud Deployment Models
There are different deployment models for cloud computing and hence each describes a way that cloud infrastructure is deployed privately or to the public.
- Public cloud computing.
- Private cloud computing.
- Hybrid cloud computing.
- Community cloud computing.
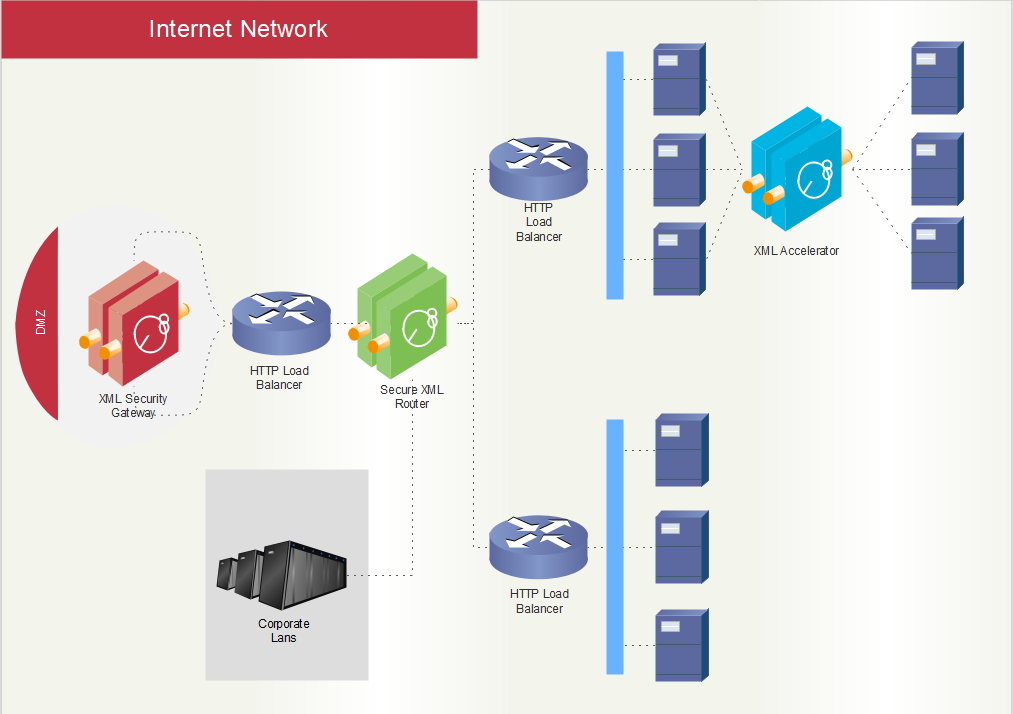
Public Cloud Computing
This will be hosted off site. It is owned by a third party company that sells cloud services to the public in a multi tenant fashion. This means they will have many customers for their services.
- This is usually available to all members of the public or large groups within an industry.
Private Cloud Computing
This is typically built to be used within an organization. It will most often be developed and run by the organization's IT department, however, it could also be held off site and run by a third party. A business might develop a private cloud offering in another geographic location so that its employees there have the same resources.
Hybrid Cloud Computing
This is just a combination of different types. A business would do this if a particular combination fit their business model better. These different cloud models will maintain their own characteristics but are bound together to form a single unit.
- They can also offer standardized access to data and applications.
- A business in the process of converting to cloud computing might use a hybrid cloud while they transition from traditional storage to cloud based storage.
Community Cloud Computing
A community cloud model is an open inter-network that enables clients to find resources on demand. This is important because it separates an organization from cloud resource providers. There are usually no contracts or agreements that are needed before clients can access the content they require.
Basic Network Requirements
To implement all of the previously mentioned communication types there are a few basic requirements that you need. I want to go over those now. Most basic networks need centralized network components like a router and a switch. There are others too that you need to make use of typical network communications. As a result, there are many kinds of devices and ideas to consider.
- Computers, laptops, tablets, cell phones, and printers.
- Routers, switches, and firewalls.
- VOIP phones, network storage, and access points.
Requirements To Consider
First, it helps if you have an idea of the number of computers, switches, and access points you will have on your network. Consequently, you will want to make sure your devices are large enough for your current needs plus any future growth.
- Internet connectivity - How much bandwidth do you need?
- Wireless connections - You will want a sufficient number of these if you choose to allow wireless at all.
- Connectivity of peripherals - Consider how many and where these will be connected.
- Access point locations - having good signal is important with the number of laptops,cell phones, and tablets that users bring to work these days.
Network Compatibility
Not everyone will have the latest technology so we need to make sure they can use our network and resources. We typically do not have to worry about Ethernet because those network interfaces have some built in backwards compatibility. Therefore, if you have multiple locations then you need to have your routers be able to work with each other.
WiFi Compatibility
The current wireless interfaces are 802.11ac and 802.11n but they will also support older wireless standards as well. So it is nice that a lot of hardware has built in backwards compatibility. You should still try to plan for using current standards if at all possible though.
Environmental Requirements
Sometimes our network and its equipment is affected by the environment. Electromagnetic interference is one of the things that can affect our network's performance. An example is our Ethernet cables can be affected by lights in our building. That is the environment lowering our performance. Another example is power cables can cause interference if they are run too closely to the Ethernet cables. Wireless interference is also something you need to pay attention to. There are lots of different kinds of wireless devices and some will certainly affect the performance of your network.
Security Requirements
Security is a very important topic. When setting up your network communications devices you will want to use private IP addresses inside your network. Use the public Ip address at your edge router so it can do its job.
- Make sure you use a firewall.
- Use antivirus and antimalware to protect yourself or your business.
- Have firewall software on your servers and clients.
- Use good physical security such as key-pad locks on the doors to your network closets.
- Access to networking equipment should be limited.
Conclusion
In conclusion, network communications encompass a large area in Information Technology and networking in general. There are many things to consider when you decide upon a certain communications standard or technology. Even among any particular communication protocol you will see that there are multiple sides to it.
Please leave a comment below to let me know how you liked this article or if you had any questions.