How The OSI Model Works
The OSI model is a theoretical framework on how networking works. It tries to tie together all of the different protocols that we depend on today to use the internet. In this guide I explain what it is in as much detail as I can and how it is used because knowing how the OSI model works can be very useful.
How The OSI Model Works Today
Most networking professionals are very familiar with the OSI model. They do not have to use it every day but it can be helpful when they have to. When used correctly it can be a type of guide to diagnose problems and understand what is happening with your network.
History Of The OSI Model
The history of the OSI model is based around networking standards. The industry needed to get all of the manufacturers on the same page and and have them all follow the same procedures. The model was created to become the foundation of all the protocols that would become the internet. So today it explains the protocols that we use every day and general networking. That is how the OSI model works and what it means to us right now.
Layers Of The OSI Model
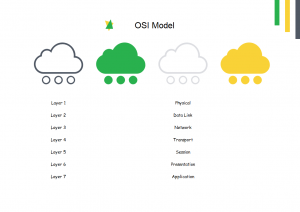
The OSi model is divided up into 7 different layers. Layers work with each other, especially the ones above and below any particular layer. They are numbered because they represent how physical and hardware oriented each layer is. The bottom layer is the physical layer that involves actual hardware while the top application layer is the most abstract. Here they are:
- Physical layer
- Data link layer
- Network layer
- Transport layer
- Session layer
- Presentation layer
- Application layer
Physical Layer
This is your network's physical attributes. It specifies what kind of networking hardware is used to transmit data and the electrical specifications that are used. Topology is also considered here as networks used to have a definite style to them. Protocols such as USB and Ethernet operate at this layer.
Data Link Layer
The purpose of the data link layer is to get data to the physical layer so that data can be sent over the network. One part of the data link layer is the Media Access Control section. This is an address built into every network card.
Network cards are the devices that let you plug a Cat-6 cable into them. The other section of the data link layer is the Logical Link layer. This section is responsible for error control to keep the transmission of data going smoothly.
Network Layer
The network layer does the routing for your network so that data gets to its destination. As in most layers, the protocols associated with that layer provides the way for that layer to work. These protocols select the path as well that the data will take over the network. Data is grouped into packets before it is sent on its way through your network.
When data is routed through a network it can be done so manually or automatically. If it is done manually it is called static routing and your routing tables are updated by the network administrator. Now if your routing is done automatically it is called dynamic and it is done through routing protocols. Protocols such as Arp, Rip, and IPsec operate at this level.
Transport Layer
The purpose of the transport layer is to provide a way for network information to travel between your network devices. Some error checking is also done here to make sure information is still valid by the time it reaches other devices. There are two main protocols that operate at this layer which are UDP and TCP.
UDP is a connectionless protocol which means that it just sends the information and does not make sure it reaches its destination. TCP is a connection protocol and so it will try to ensure the data goes where it is supposed to.
Session Layer
The function of the session layer is to control the data between applications over the network. It does this by creating and ending sessions. Sessions help maintain data integrity by isolating the data from other network traffic. This is another way the session layer controls the information. Protocols that work at this layer are SMB and NFS.
Presentation Layer
The purpose of this layer is to convert data to a format that will travel over the network well. Media formats are usually what is handled here by this process. Examples are Jpeg, Mp3, and Tiff files. Since data is handled here, encryption is done at this layer too. Encryption is the process of making information unreadable to humans. The TLS protocol operates at this layer.
Application Layer
The main function of the application layer is to take requests by humans that are input into applications and make sure that input is sent to the lower levels of the OSI model. Information can also be shown to users by the application layer when the data comes from the lower levels of the model.This layer does not represent actual applications on your computer but gives them the functionality to pass data on through the network.
Important Protocols
While the OSI model is theoretical for the most part, the protocols that use it are what gets things done. They enable all of the functionality and make it possible for our network traffic to get where it is supposed to be. There are many important protocols that the internet and our private networks depend on. DHCP, DNS, SNMP, TCP, and IP are probably the most well known so I will talk about those.
However, there are several more that are just as manadatory for network traffic to use. To understand how the OSI model works, you need to know how these protocols integrate into it.
DHCP
This stands for dynamic host configuration protocol and it is very important in large business or organizations. This protocol software is set up on a server and it will automatically assign IP addresses to your clients so you do not have to manually enter them in.
These addresses are big blocks of available addresses that DHCP can use. They are known as scopes which is the term that networking people like to use. Addresses are assigned to client computers from this range of IP's by DHCP and this technique is known as dynamic addressing.
You can also input all of the Ip addresses into computers one at a time and this is known as static addressing. It is ok for like 5 computers but if you have 500 computers in your network then that would be a real pain.
When DHCP gives a computer an IP address it is usually for a finite amount of time. This is the lease of the IP address and it is important to remember because at the end of the lease it will expire and another one will have to be assigned by the DHCP server. You will get a warning when the lease is close to expiring so you can plan ahead if you need to.
Now lets talk about reservations. DHCP reservations are assigned to network devices when you do not want the IP address to change. This is useful for devices like a printer or network switch. It is useful because you do not want those types of devices to change their IP address.
DNS
DNS is one of those protocols that is just a pleasure to have around. I know most of you will have heard of it and know what it does. However, have any of you really thought about the convenience it offers? I had not either until recently but now I am so glad we have this. So what does it do for the uninformed?
It takes a name that you put in your browser address window and does its magic to make that website appear for you. Specifically it resolves hostnames which are the names of websites. These hostnames and any subdomains within them are called FQDN's which stands for fully qualified domain name.
A great attribute of DNS is that it runs on almost any operating system. Operating systems such as Windows, RHEL, Ubuntu, Suse, BSD, and Solaris will all run DNS and that is a marvelous thing.
For a little perspective, sites and their IP information would have to be manually entered into a text file. This was not a big deal when you only knew of 3-5 internet sites but now will millions hopefully you can see how important DNS is.
Types Of DNS Records
If you have ever operated and run your own website then you know that dealing with DNS records is a part of life. In fact, there are several DNS records that go together to help your website get online. You will just enter this information with your domain host and that should get you going. Some examples of these are:
- Name Server - identifies the name servers that where your information is hosted
- CNAME - this record will give an alias to your hostname
- IPv4 - this is the one that maps a hostname to an address
- Mail Exchange - this tells your email where to go
SNMP
This protocol is a little more abstract and not as familiar to many people. It is the protocol that enables network management software and stands for simple network management protocol. Network management software and the analytics associated with it are very popular in recent days. Since it allows you to know what is happening with your network at any given moment, it is extremely useful.
The SNMP software works by having software agents listen for specific events that happen. Once any of these predefined events happen then the agent reports back to the software manager. The agents can monitor about anything but typically it watches switches, routers, servers, and printers.
There is also limited functionality here too as the devices can be controlled to some extent and the network person can perform basic tasks on the devices.
You can also issue commands to the system to get more information at a particular time. The commands are typically simple but they can do a lot by using GEt, Set, and Walk.
IP
This stands for internet protocol and is responsible for moving traffic from one network device to another. It is also a connectionless protocol which means that it just sends the data on to where it is supposed to go. IP does not check to see if the data made it to its destination because it is connectionless.
It works in conjunction with the TCP protocol for more reliability. The IP protocol works at the network layer of the OSI model.
TCP
This is the transmission control protocol that makes the IP protocol work better. It works by using sessions and by making sure adequate communication can take place between two clients. TCP is a connection oriented protocol which means that it makes sure all the data reaches its destination.
Error handling is also an important part of what TCP does because it does its best to watch for errors in transmissions. TCP operates at the transport layer of the OSI model.
UDP
This stands for user datagram protocol and is very similar to TCP. There are major differences though because UDP is connectionless and does not check to see if its data transmission made it to the end. A nice advantage of UDP is it's efficiency over TCP.
Since it is so much smaller it can run much faster than TCP. When the writers of applications are coding they will sometimes use the UDP protocol if they do not need the extra features of TCP.
FTP
This is a very old protocol and has been around for many years. It stands for file transfer protocol and it is used to transfer files between a server and a client. FTP can be used to distribute files to the public, friends, or even to yourself if your in different locations occasionally.
The FTP protocol is still used a lot today and has a large gathering of followers. There are graphical as well as command line applications.
Typical FTP Commands
Here are the most used commands when you use an FTP command line client.
- ls
- cd
- lcd
- put
- get
- mput
- mget
- binary
- ascii
SFTP
This is a newer and more secure version of FTP. It stands for secure file transfer protocol. One of the reasons it is more secure is that it does encryption as well as not sending information in a readable format. It is also used in a server and client set up.
I have used one of these clients when uploading information to this web server before. Obviously I did not want to use plain FTP over the internet so I went with SFTP. Like FTP, there are many clients and versions of software to choose from.
SMTP
I am sure by this point you may have had enough of confusing acronyms but there are only a few more and this is one of them. SMTP stands for simple mail transfer protocol and it is responsible for how email is sent between 2 clients. It is an older protocol but it is still used quite a lot. It uses port 25 by default and can subsequently be used to send and receive mail at the same time.
HTTP
Now I bet you have heard of this one as it is probably the most well known. It is the hypertext transfer protocol and allows an individual to download information like text and pictures from a web server. This website is on a computer which has a web server installed on it. The HTTP protocol allows you to see my articles that I write in your web browser. HTTP uses port 80 by default to communicate with web servers. It is also a connection oriented protocol because when you load a website you want to see everything there.
HTTPS
This stands for hypertext transfer protocol secure and is obviously the secure version of HTTP. The main difference between the two protocols are that HTTPS encrypts its requests to protect information. Most everything now supports HTTPS.
SSH-Secure Shell
Secure Shell is a very useful tool and is the secure version of telnet. Encrypting your information is one of its important duties. You do not want your log in to travel travel to your server in plain view of everyone because it could get stolen. Many use this to log in their remote servers by using this this method.
Internet Control Message Protocol
Reporting data is what ICMP is all about. In its functional form we are talking about the ping utility. I use this all the time to check the status of computers and printers. If someone is having trouble getting connectivity then you can use ping to see if it is truly the connection or some application on the computer. Another use is to check if a printer is on a certain IP address. Just ping it to see if it responds.
Conclusion
I know that is a lot of terms and acronyms today but they are fundamental concepts in computing. Networking is a huge topic but it has many areas of interest.